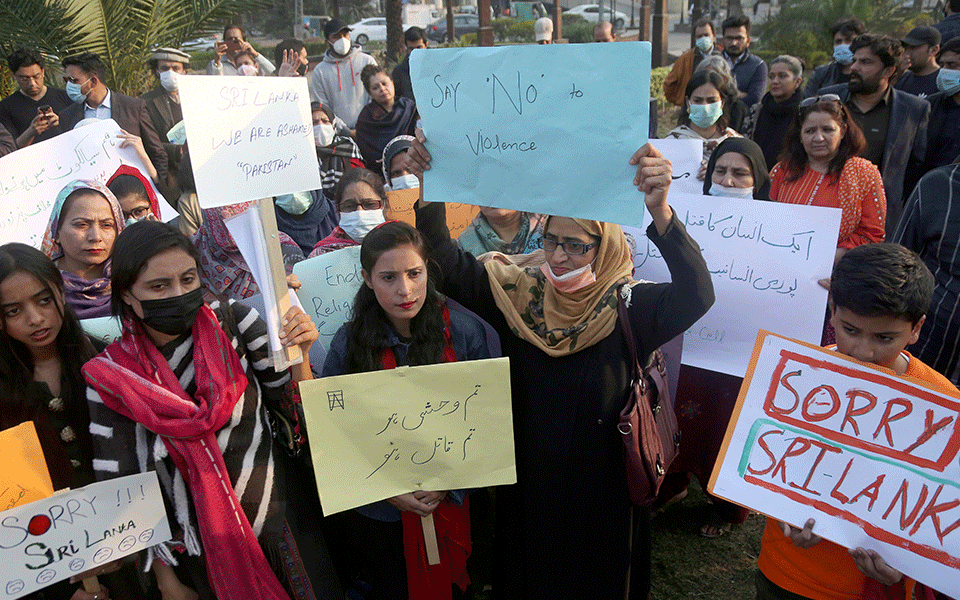Colombo(PTI): The grieving wife Sri Lankan national Priyantha Kumara Diyawadana, who was lynched over allegations of blasphemy in Pakistan, has pleaded for justice from both the Pakistani and Sri Lankan governments, saying her husband was a very innocent man.
In a shocking incident on Friday, angry supporters of the Tehreek-e-Labbaik Pakistan (TLP) attacked a garment factory and lynched its general manager Diyawadana before setting his body on fire over allegations of blasphemy.
As pressure mounted on the Pakistani government to bring the guilty to justice, over 800 people have been booked under terrorism charges while 13 prime suspects are among 118 arrested so far in the horrific lynching of the Sri Lankan national in Punjab province.
I got to know about the brutal murder of my husband from the news, later I saw this on the internet as well. He was a very innocent man, she was quoted as saying by BBC Sinhala.
I request leaders of Sri Lanka and Pakistan to do justice for my husband and two children, by bringing the perpetrators to justice, she said.
Sri Lanka's NewsWire website reported that Ministers Namal Rajapaksa and Prasanna Ranatunga on Saturday visited the residence of Diyawadana in Ganemulla, about 22 kms from here.
Diyawadana, a graduate from the University of Peradeniya, is survived by his wife and two children.
He left for Pakistan for employment in 2010 and has been working as the manager of the Sialkot factory since 2012.
Meanwhile, Sri Lankan High Commissioner in Pakistan Vice Admiral Mohan Wijewickrama said that arrangements are being made to transport the mortal remains of Diyawadana on Monday from Lahore to Colombo in a special flight, the NewsWire reported.
Diyawadana, who was in his 40s, was working as the general manager in the Rajko industries (dealing in garments sportswear) in Sialkot district, some 100 kilometres from Lahore.
Sri Lankan Parliament and Prime Minister Mahinda Rajapaksa on Saturday condemned the lynching and hoped that Prime Minister Imran Khan will keep his commitment to bring all those involved to justice and ensure the safety of the rest of the island nation's expat workers.
A mob of over 800 men gathered at the factory at 10 am Friday on reports that Kumara had torn a sticker/poster (inscribed with Islamic verses) and committed blasphemy. They looked out for him and found him (from the rooftop). They dragged him, beat him severely and by 11.28 am he was dead and the body was set on fire by the violent mob, Inspector General of Police (Punjab) Rao Sardar Ali Khan said.
The mob after burning the body of the Sri Lankan national had blocked the Wazirabad road. Police from different stations reached there to control the situation, he said.
The incident sparked widespread condemnation from all walks of life. Police were also chided for reaching the crime scene after the incident. Only a couple of policemen can be seen in one video asking the people to stay back while the body was burning.
In April 2017, an angry mob lynched university student Mashal Khan when he was accused of posting blasphemous content online.
A Christian couple was lynched and then set ablaze in a kiln in Punjab in 2014 after being accused of desecrating the Quran.
Let the Truth be known. If you read VB and like VB, please be a VB Supporter and Help us deliver the Truth to one and all.
New Delhi: India’s national cybersecurity agency, the Indian Computer Emergency Response Team (CERT-In), has issued a high-severity alert warning WhatsApp users of an active account takeover campaign using a new technique known as “GhostPairing," in an advisory released on December 19.
CERT-In said cybercriminals are exploiting WhatsApp’s device-linking feature to gain unauthorised access to user accounts without the need for passwords or SIM card swaps, as reported by The Indian Express. The attackers, the agency warned, deceive users into entering pairing codes, which silently grants control of the account to a malicious device.
ALSO READ: Teen killed in alleged honour killing over inter-community relationship, brother, his friend arrest
According to CERT-In, the GhostPairing method works by tricking victims into approving an attacker’s browser as a trusted linked device. The advisory said, “The attack manipulates users into granting access through a pairing code that appears legitimate." It further added that once access is granted, attackers can fully operate the account through WhatsApp Web.
Last month, the Department of Telecommunications directed messaging platforms such as WhatsApp, Signal and Telegram to implement continuous SIM binding which required accounts to remain linked to an active SIM card. As part of this directive, companion web sessions are expected to be logged out periodically and re-authenticated using QR codes.
CERT-In said the GhostPairing campaign typically begins with a message appearing to come from a trusted contact, often reading, “Hi, check this photo”. The message contains a link designed to mimic a Facebook-style preview, and clicking the link leads users to a fake verification page, where they are prompted to enter their phone number and a code. Victims unknowingly allow attackers to link their WhatsApp account to an external device, by completing these steps,.
Once compromised, attackers can access messages, photos, videos and voice notes in real time, and can impersonate the victim to send messages to individual contacts or groups, the agency said.
The advisory also noted that WhatsApp currently allows multiple devices to be linked to a single account, a feature that is being misused in such attacks. In October, the Indian Cybercrime Coordination Centre under the Ministry of Home Affairs had flagged a related trend involving scammers using social media advertisements to lure users into linking their WhatsApp accounts.
While the government’s SIM-binding push is intended to limit such fraud, it has raised concerns among legal experts and digital rights groups, who argue that constant SIM verification, could affect privacy and disrupt multi-device usage, particularly for professionals.
To reduce risk, CERT-In has urged users to avoid clicking on suspicious links, even if they appear to come from known contacts, and to never enter phone numbers or verification codes on external websites claiming to be linked to WhatsApp or Facebook. Users have also been advised to regularly review the “Linked Devices” section within WhatsApp settings and immediately log out of any unfamiliar sessions.
For organisations relying on WhatsApp for communication, the agency has recommended security awareness training, closer monitoring for phishing attempts, and the establishment of clear response protocols to detect and contain account compromises quickly.